Know the threats. Reduce your risk exposure. Be resilient.
Today’s global cyberattacks pose an increased threat to our daily lives with real-world, far-reaching consequences such as economic loss, social upheaval, and even political instability. As generative technology advances and the world becomes increasingly connected, timely detection of cyberattacks is the first step in protecting your networks, data, digital assets, and hybrid infrastructure from ruin. Get the tools and resources you need to understand how to protect your organization from cyberattacks and drive perpetual resilience with this year’s Global Threat Intelligence Report.
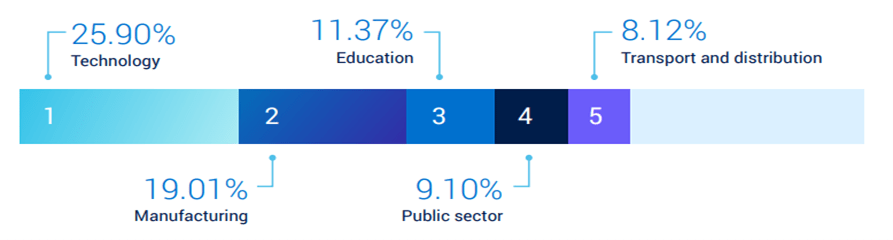
Top 5 most-attacked sectors
Technology, manufacturing, and transport/distribution remained in our top five most-attacked sectors, with critical infrastructure and supply chain remaining high-value targets. The public sector also made the biggest jump in the past year, moving from #6 to #4.
Key findings from this year’s report
Cloud and SaaS attacks
Web based applications and desktop applications made up 70% of cyberattacks with a 45% and 25% attack-split to web vs application use. This trend was popular in critical vulnerabilities that exist in products such as JIRA, Confluence and Bitbucket to mention a few.

